compromise assessment malaysia
Our compromise assessment service has been designed to answer that question. Bank Negara of Malaysias Risk Management in Technology.

Ioa Vs Ioc Defining Understanding The Differences Crowdstrike
What is Compromise Assessment.
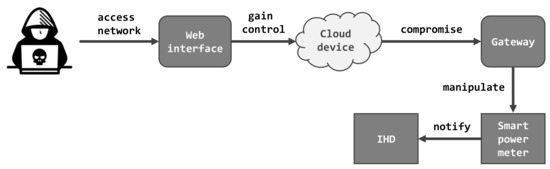
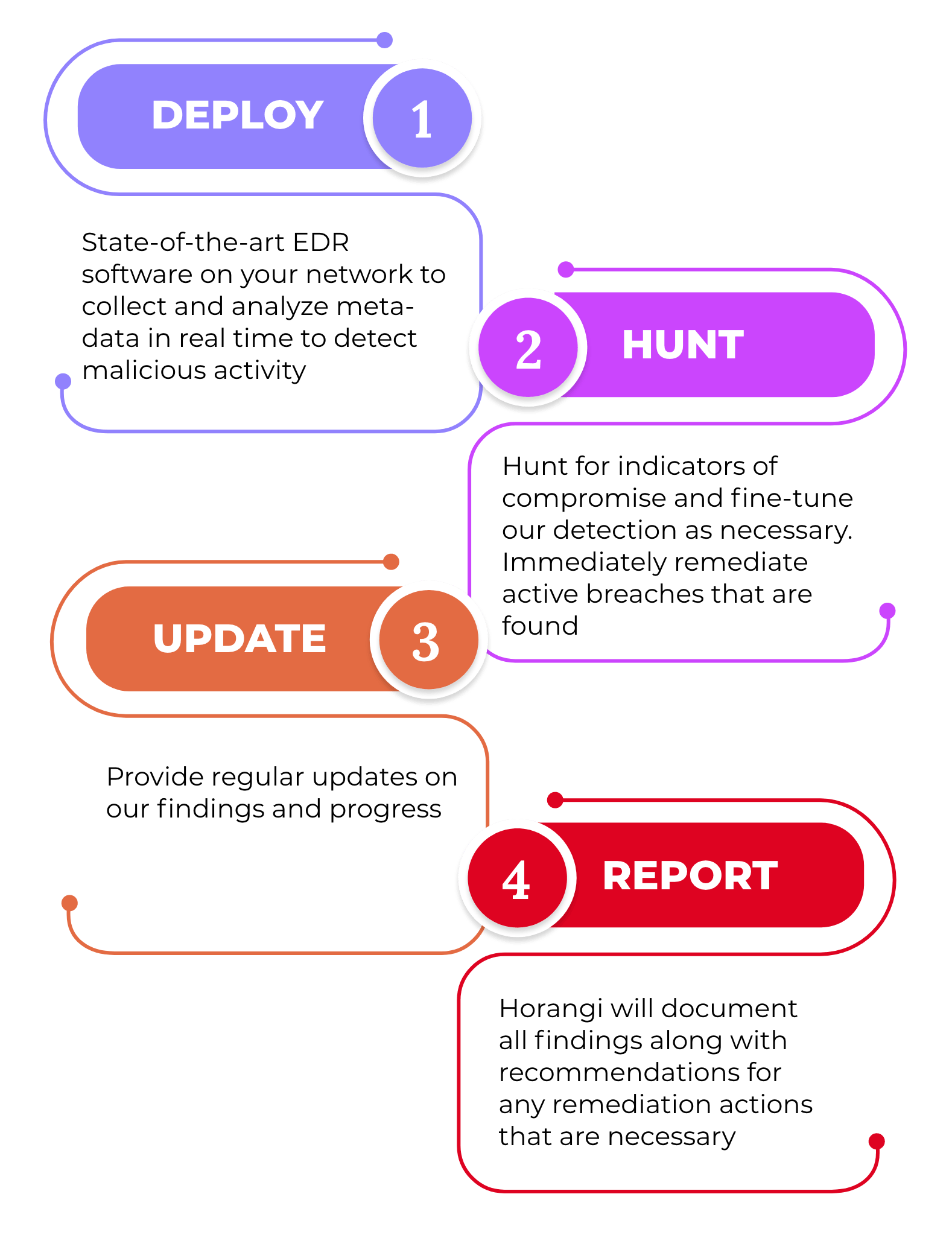
. Compromise Assessment is a high-level review of the security posture of an organization to identify if they are already compromised or breached. Our Compromise Assessment Services Team walks you through fully-actionable eradication plans explaining each step simply and clearly. The approach is designed to be light-touch with simple and temporary monitoring installations.
3 Identify security weaknesses in the current system. Compromise assessments CA answer the fundamental cyber security question Are we breached. In an interview with Information.
Thats why our methodology involves looking at every possible forensic artefact behaviour and traffic in an environment and conclusively validating its level of risk to business Endpoint Forensic-Depth Analysis. He further explained that in Malaysia a compromised assessment is an exercise required by the local central bank to ensure the financial institutions FIs gain visibility to answer three basic questions. Our Compromise Assessments are an essential business need for all organisations.
Compromise Assessment Firmus 2020-06-14T1449110800. During the assessment we found live evidence of the early stages of a WastedLocker ransomware attack. With a typical end-to-end duration of approximately seven to nine.
Pursuant to the investigation the MIHSOA undertook via a letter of undertaking dated 30 January 2014 to among others. Our threat hunters will combine state-of-the-art targeted cyber threat intelligence network and endpoint detection to review your organizations infrastructure systems and applications in order to identify malware back-doors unauthorized access and indicators of compromise which could confirm. The Malaysia Indian Hairdressing Saloon Owners Association MIHSOA the MyCC found that the agreement by members of MIHSOA to increase the price of their haircut services by RM2 amounted to an infringement of the Chapter One Prohibition.
Cybersecurity Posture and Maturity Assessment. Understanding when we are breached and resolving it should be the top priority. They want to know if youre compromised can identify the compromise and if you can come up with an effective incident response strategy.
Malaysia through operations of branches and subsidiaries. 2 To identify the presence of any security breaches. We were able to rapidly analyse the malicious activity for additional indicators of compromise and sweep the entire environment for any signs that the threat actor had moved laterally across the network.
In an increasingly complex and dynamic threat landscape now more than ever organizations need to understand the effectiveness of. While penetration tests focus on finding vulnerabilities a compromise assessment focuses on whether an organization was breached without knowing it he explains. 樂 Why has Bank Negara Malaysia BNM mandated Large Financial Institutions to perform Compromise Assessment.
OTP or one-time password refers to an alphanumeric or numeric code. When conducting compromise assessments the priority must not be to reduce false-positives but to reduce false-negatives. Compromise Assessment Needs 1 To comply with local laws regulations Eg.
Material technology projects refers to projects which involve critical systems the delivery of essential services to customers or counterparties or compliance with regulatory requirements. Secure Software Development Lifecycle. We then transitioned the investigation to our Incident.
Our CA service delivers a high-level review and audit of your organizations IT environment based on suspicious user behaviors logs compliances policies Indicators of Compromise IOCs or any evidence of malicious activities to identify attackers currently. Vigilant Asia is an award-winning MSSP delivering compromise assessment services in Asia using ThreatDefence XDR platform. Using Deloittes Cyber Compromise Assessment CCA on your estate will help identify if there is a current or indicators of a past compromise of your network - utilising the latest threat intelligence and detection techniques.
It takes organizations an average of 191 days to identify a data breach. In this upcoming webinar CEO of LGMS MrFong Choong. Increasingly companies around the world understand that Compromise Assessments are a basic business imperative as they enable them to.
THOROUGH We rescan and confirm eradication with cyber threat intel from multiple major proprietary sources organizations across the globe and through our rigorous AI-driven vetting process. Comply with industry regulations Avoid straining customer relationships as a results of breaches and leakage of sensitive data. Cyber Security Gap Analysis and Roadmap Development.
Compromise Assessment checks if any attacker activity or unauthorized access is already present in your network by analyzing data logs and existing telemetry to identify.

Compromise Assessment Condition Zebra Cyber Security Company Malaysia
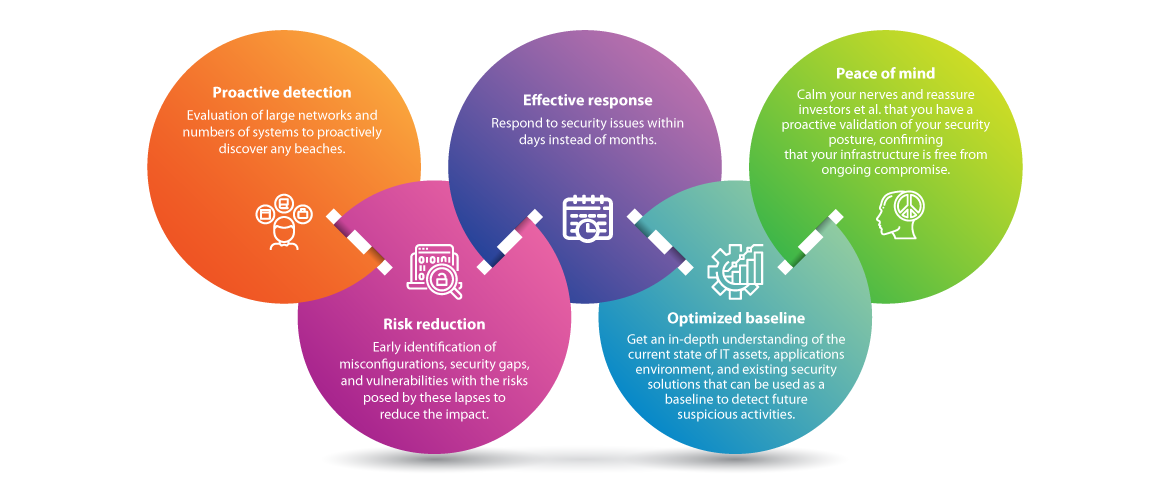
Key Benefits Of Compromise Assessment Infographic Ec Council Global Services Egs

Applied Sciences Free Full Text Threat Modelling And Beyond Novel Approaches To Cyber Secure The Smart Energy System Html

Compromise Assessment 7 Things You Should Know Lgms Blog

Compromise Assessment Malaysia Uncover Hidden Security Risks Firmus

Indicators Of Compromise Definition

Compromise Assessment Cybereason Assessments
What Is Compromise Assessment The Benefits How It S Different How By Cycraft Technology Corp Cycraft Medium

Media Exp1 Licdn Com Dms Image C5112aqf6apbivoucuq

Compromise Assessment Ec Council Global Services Egs

Ioa Vs Ioc Defining Understanding The Differences Crowdstrike

Compromise Assessment 7 Things You Should Know Lgms Blog

Cyber Compromise Assessment Deloitte China Risk Advisory

The World Cup Is Here And With It Comes Excitement Pride Competition And Sportsm Physical Education Lessons Education Lesson Plans Physical Education Games
Cyber Security Compromise Assessment Services From Cyberstash
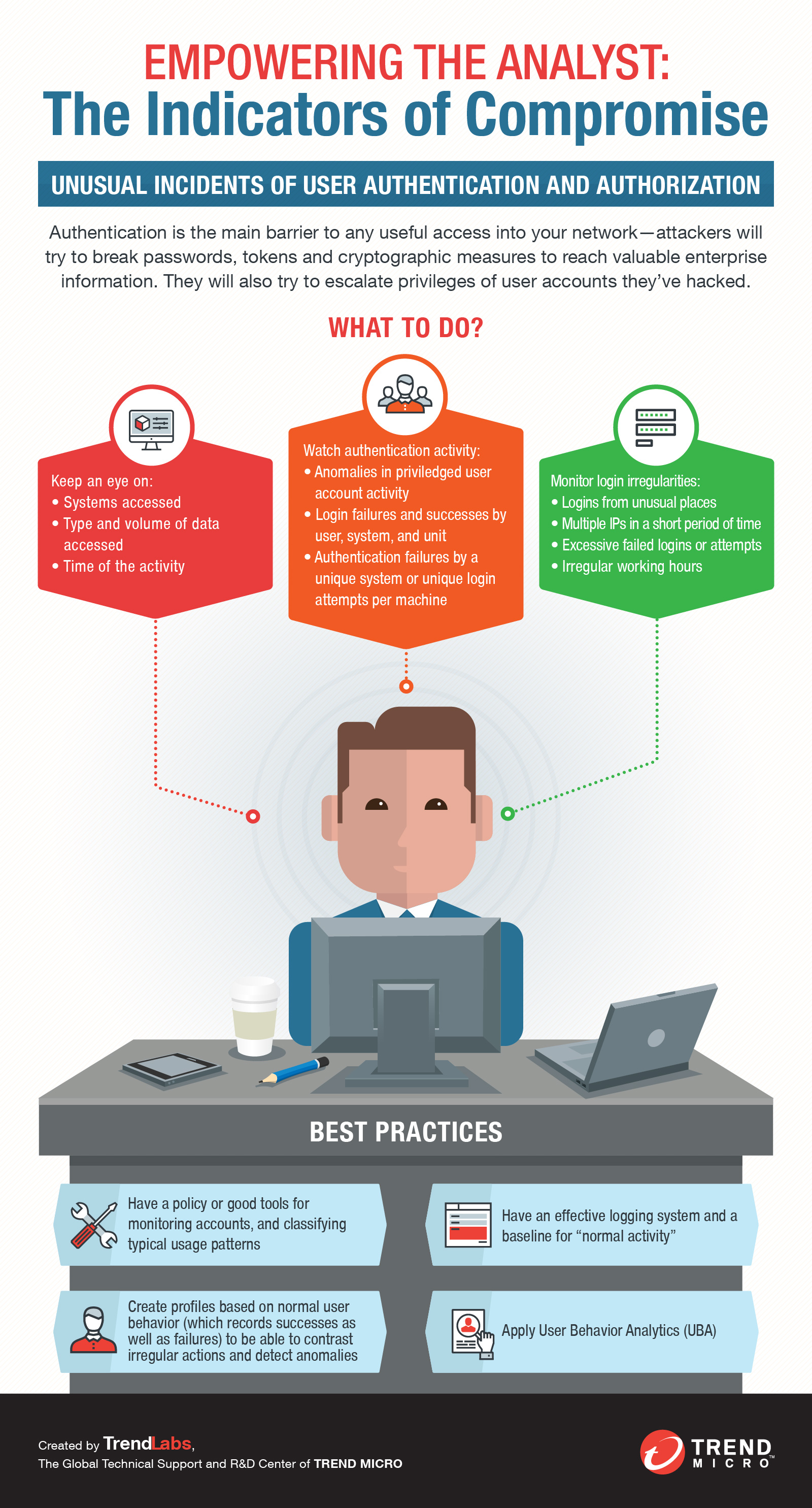
Indicators Of Compromise Definition







0 Response to "compromise assessment malaysia"
Post a Comment